Why You Should Attend
SecurityBSides Milano Conference
Networking
The goal is to create opportunities for individuals to participate in an atmosphere that encourages collaboration and spontaneous conversations.
Learning
Trying to be on-the edge, learning from peers on specific technical subjects
Spark New Ideas
It is an intense day with discussions, demos, and interactions from participants. It is where ideas for the next-big-thing are born. It's where you can build lasting connections.
Sign Up to the conference
Before Registration Closed
Underground CyberSecurity Conference - WorldWide
Each BSides is a community-driven framework for building events for and by information security community members. The goal is to expand the spectrum of conversation beyond the traditional confines of space and time. It creates opportunities for individuals to both present and participate in an intimate atmosphere that encourages collaboration. It is an intense event with discussions, demos, and interaction from participants. It is where conversations for the next-big-thing are happening.
Speakers
Courses
Our Provided Perks For You
During Conference
Thanks to our amazing sponsors and community donations we were able to
provide different benefits
We all hope you are going to enjoy them!
Beer
T-shirts
Gadgets
Dinner
CTF
Experts from all over the
Globe Sharing Experence, their stories, their expertise!

Matteo Rosi

Vito Alfano

Cristian Cornea

Orlando Barrera II

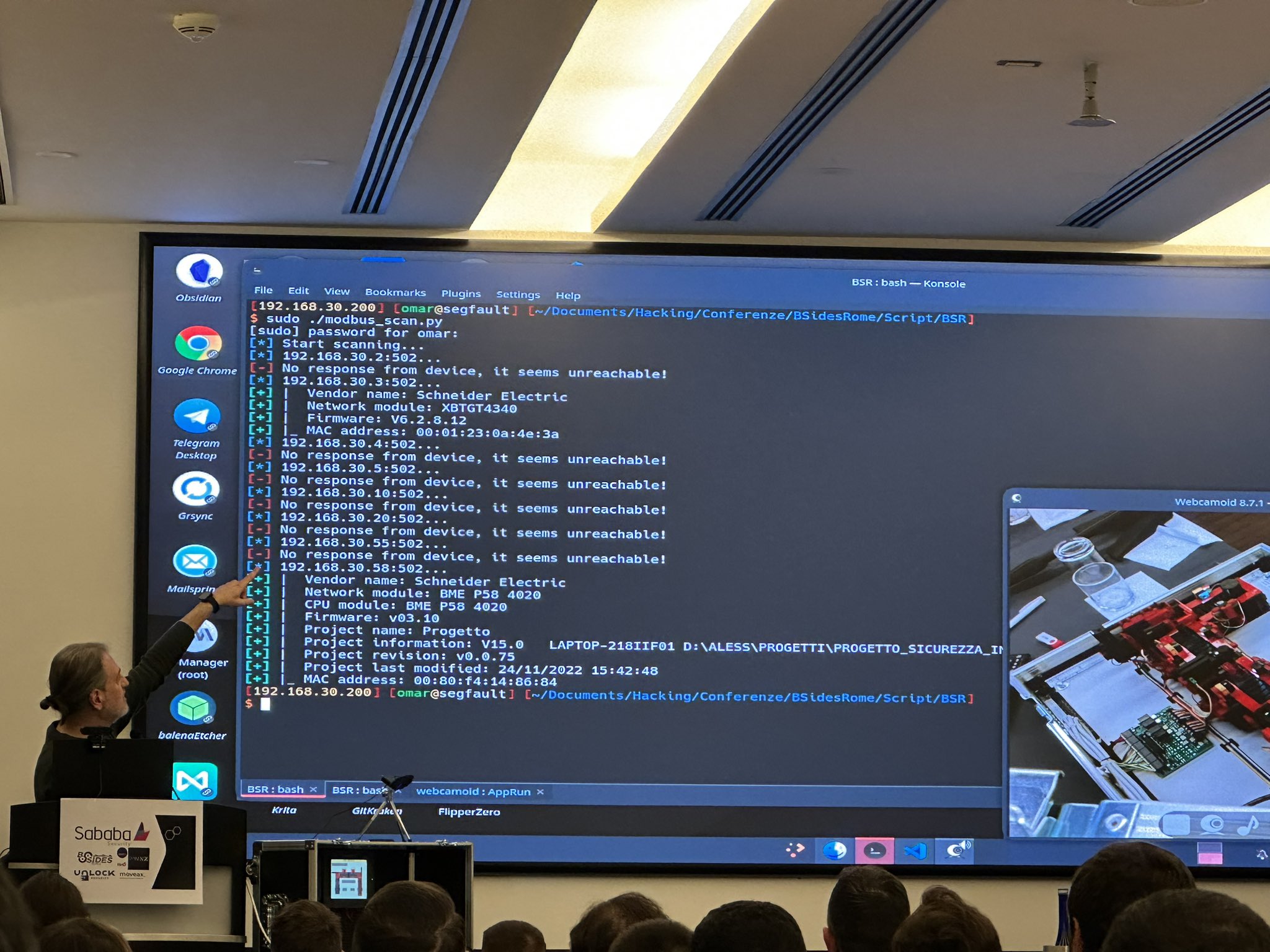
Omar Morando

Claudio Merloni

Antoine Carossio


















